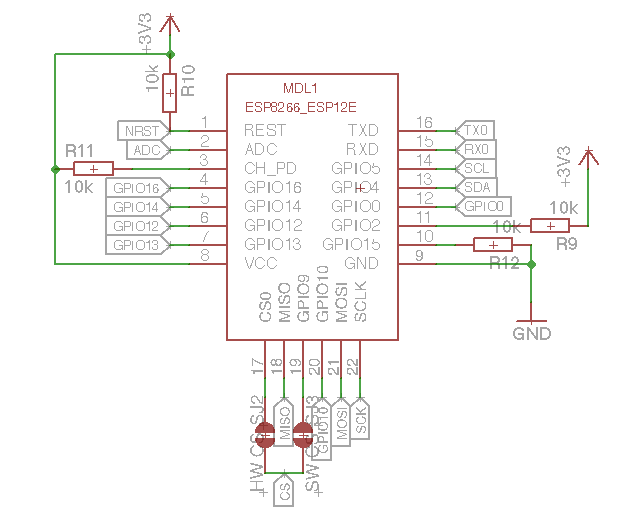
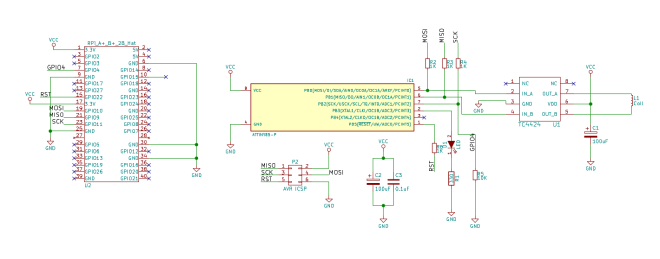
Electronic Cats made an important commit at SamyKam schematics. The first version of the PCB had an issue with a ground for the rotary encoder. The switch to select things in the menu was not working properly. After the fix, I tested the last version of the SamyKam PCB today from Oshpark, and […]
security
Samy Kamkar Illustrates How to Be a Hardware Hacker
From Hackaday Supercon last month in Pasadena, California:
Samy Kamkar Illustrates How to Be a Hardware Hacker
Samy Kamkar is well known for many things, but lately it has been his hardware security hacks that have been turning heads. The nice thing to know is that, despite not having a background in hardware, Samy is able to run with the best of hardware researchers
ESPTool: WiFi Security Swiss Army Knife
Daniel Grießhaber created this convenient tool to test your WiFi Security against attackers:
ESPTool
Demonstrate how easy it is to crack a WiFi Password or jam your WiFi so you can’t access the internet. Designed for education and self-tests.
ESPTool has the following hardware:
- SSD1306 based OLED Display, connected via I2C
- microSD Card Socket connected over the SPI interface
- 3 general purpose buttons
- ESP8266-12E Module
- TPS63031 Buck-/Boost-Converter with an input range from 1.8V – 5.5V
- MCP73831 Single-Cell LiPo Charger Chip
- CP2012 USB to UART converter Chip
The design files and source code are available on GitHub:
 dangrie158/ESPTool
dangrie158/ESPTool
MagSpoof for Raspberry Pi
Be able to make & upload MagSpoof with variable tracks, to use it without Arduino dependencies, and implement it on the same Raspberry GPIO.
More details are available on Salvador’s blog.
The makefile and the modified MagSpoof library are avialabel on GitHub:
 MagSpoofPI
MagSpoofPI
Optical Convert Channels
One of our favorite hardware hackers, Joe Grand, has shared slides and hardware designs from his recent B-Sides PDX talk:
Optical Covert Channels
Data exfiltration from a device is usually achieved over the network, via hardware implant, or by manipulating the characteristics of an internal electronic component. Optical covert channels transmit data using visible light in a method undetectable to the human eye.
Joe demonstrates using an optical receiver to capture data transmitted through a LED:
joegrand has shared the receiver boards on OSH Park:
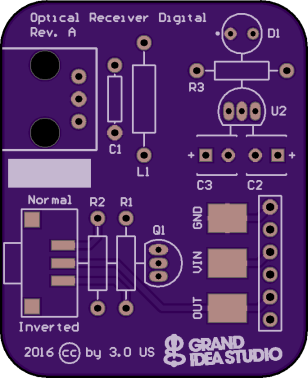
OpticSpy Digital (Rev. A)
digital version using Everlight PLR135/T9 Fiber Optic Receiver
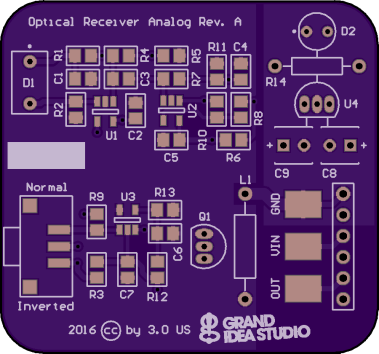
OpticSpy Analog (Rev. A)
analog version based on Maxim Integrated’s AN1117 application note: